Key takeaways:
- Online payment security is a combination of strategies that protect online transactions from growing security threats.
- In addition to software and hardware components, regulatory compliance also helps prevent unauthorized access to your customers’ payment (and other sensitive) information.
- Your online payment security strategy should cover all stages of an online transaction from the point where customers access your system.
- A data breach caused by insufficient security infrastructure can cause monetary and reputational damage to your business.
What is online payment security?
Online payment security is the framework of technologies, protocols, and entities that work together to protect electronic financial transactions. It ensures the confidentiality, integrity, and availability of payment data throughout the entire transaction lifecycle from the moment a customer initiates payment to the final settlement with a merchant or service provider.
Ensuring a secure payment system is crucial for protecting customer trust, avoiding financial losses, maintaining regulatory compliance, and preventing identity theft and cyber fraud
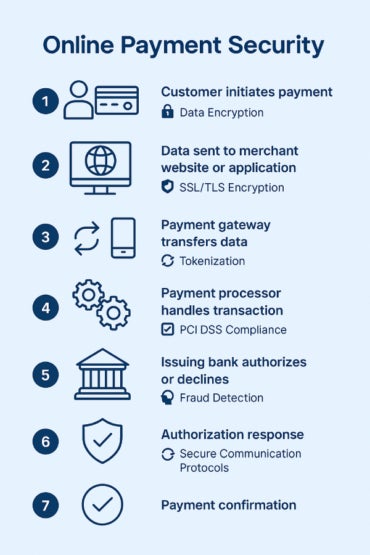
The key components of online payment security are made up of software and hardware infrastructure:
- Firewall: Acts as a barrier between internal systems and external threats by filtering incoming and outgoing network traffic, blocking unauthorized access attempts
- SSL and TLS certificates: Enable encrypted communication between a user’s browser and the server, protecting sensitive data, such as credit card numbers, during transmission
- Fraud monitoring tools: Use behavioral analytics and machine learning to detect suspicious activity in real-time, flagging or blocking potentially fraudulent transactions
- PCI-compliant payment processor: Ensures the handling of cardholder data meets strict security standards, including encryption, tokenization, and secure storage — reducing risk for merchants
- Password-protected business terminals: Prevent unauthorized physical and digital access to sensitive systems, especially when paired with multi-factor authentication and device-level encryption
- Device management tools (MDM): Especially for remote teams, MDM solutions allow companies to manage, encrypt, and wipe devices if they’re lost or compromised
These features work together to establish a layered defense, helping organizations secure their online payment environments from end to end.
Common threats to payment security
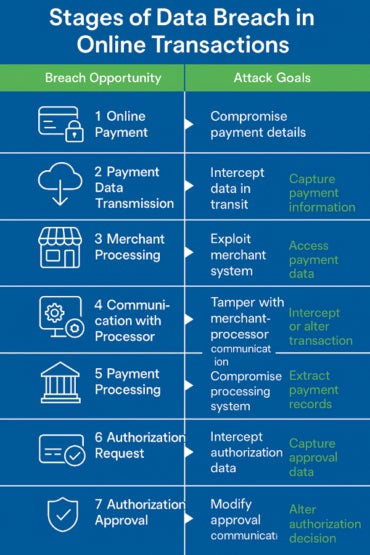
Online payment systems face various security threats at each stage of a transaction. This begins at payment initiation, where users are vulnerable to phishing, malware, and credential theft. Here, attackers often trick customers into revealing sensitive information via fraudulent emails or fake checkout pages
During the data transmission stage, cybercriminals can exploit unsecured or poorly configured SSL/TLS connections through man-in-the-middle attacks, intercepting sensitive data as it is transmitted to the merchant’s server.
Once at the merchant processing stage, attackers may leverage website vulnerabilities or gain access through insider threats to retrieve stored cardholder data or inject malicious scripts.
Further threats arise during communication with the processor, where insecure APIs or misconfigured integrations open the door for tampering or transaction interception.
In the payment processing stage, threat actors target backend systems to extract transaction records or manipulate data flows. During the authorization request, attackers may intercept approval tokens or use stolen credentials to imitate valid requests.
Finally, in the authorization approval stage, manipulation of confirmation messages or delays in syncing can allow hackers to alter the outcome of a transaction. Together, these threats underscore the critical need for robust, multi-layered security measures across the entire payment lifecycle.
See: Payment Fraud Detection and Prevention Guide
Essential payment security technologies
To combat security threats, essential payment security technologies form the backbone of secure e-commerce operations. It helps to prevent fraud, data breaches, and unauthorized access at every stage of the payment process. Below is a summary that explains how each key payment security technology works.
| Technology | Function | Layer of protection | Primary benefits |
|---|---|---|---|
| Encryption | Converts sensitive data into unreadable code | Data Transmission Layer | Prevents data interception and eavesdropping |
| Tokenization | Replaces card data with a non-sensitive token | Data Storage & Processing | Reduces PCI scope; prevents data misuse even if breached |
| 3D Secure & MFA | Adds customer identity verification at checkout/login | User Authentication Layer | Prevents unauthorized use of payment credentials |
| Secure payment gateways | Routes and protects transaction data from start to finish | End-to-End Transaction Flow | Ensures compliance, encryption, and safe third-party handling |
| Fraud detection algorithms | Analyzes behavior to detect anomalies and fraud patterns | Transaction Monitoring Layer | Blocks suspicious transactions before they settle |
Encryption
Encryption is the process of converting readable data into coded, unreadable information using cryptographic algorithms. In the context of online payment security, encryption plays a crucial role in ensuring that sensitive data, such as credit card numbers and login credentials, remains protected as it is transmitted between the customer, merchant, and payment processor.
This protection prevents unauthorized parties from intercepting or deciphering the data during transmission, particularly in scenarios involving man-in-the-middle attacks or breaches on unsecured networks.
Tokenization
Tokenization is a security technique that replaces sensitive payment data, such as credit card numbers, with a unique, randomly generated token that has no exploitable value. This token acts as a placeholder and is useless to anyone who intercepts it, as it cannot be reverse-engineered to retrieve the original data.
By eliminating the need to store actual cardholder information, tokenization significantly reduces the risk of data breaches and supports compliance with PCI DSS standards, making it a vital component in secure online payment processing.
3D Secure and multi-factor authentication (MFA)
These are advanced verification methods used to enhance the security of online payments. 3D Secure, such as Verified by Visa or Mastercard SecureCode, introduces an additional authentication step during checkout to confirm the cardholder’s identity. Meanwhile, MFA requires users to provide two or more types of identification, such as a password combined with a one-time passcode (OTP) or biometric verification.
Together, these methods add a crucial layer of identity verification, making it significantly harder for attackers to complete fraudulent transactions using stolen card details. They also defend against brute force and credential-stuffing attacks, helping to secure both user accounts and financial transactions.
See: What Are Biometric Payments?
Secure payment gateway
Secure payment gateways are third-party services that manage the routing of payment data between merchants, banks, processors, and card networks. They play a central role in facilitating online transactions by ensuring that sensitive information is transmitted securely.
These gateways utilize technologies like SSL/TLS encryption and tokenization to protect data throughout the payment process. By preventing merchants from directly handling raw card details, secure gateways help reduce the risk of data exposure, lower the burden of compliance, and significantly improve the overall security posture of an e-commerce business.
See: Best Payment Gateways
Fraud detection algorithms
These are AI-driven or rule-based systems designed to analyze transaction data in real time to identify anomalies or patterns commonly associated with fraudulent activity. These systems monitor behaviors such as unusually high transaction values, purchases from atypical locations or devices, and rapid-fire order attempts.
By flagging this suspicious behavior, fraud detection tools can automatically block or hold questionable transactions before they are completed, helping businesses minimize chargebacks, prevent financial losses, and maintain customer trust.
Compliance and regulatory requirements
In addition to technology, ensuring online payment security also requires meeting specific compliance and regulatory standards that govern how payment and customer data are collected, transmitted, and stored. Below are some of the most significant frameworks that e-commerce businesses must understand and implement.
Payment Card Industry Data Security Standard (PCI DSS)
The PCI DSS is a global security standard established by major credit card companies, including Visa, Mastercard, and American Express, to protect cardholder data. Any business that stores, processes, or transmits credit card information must comply with PCI DSS requirements.
These include maintaining a secure network, encrypting cardholder data, implementing access control, and regularly monitoring systems. Compliance helps reduce the risk of data breaches and ensures the business meets the baseline security expectations in the payments ecosystem.
💡PCI DSS (4.0) took effect in April of this year. This latest version gives particular focus on e-commerce transactions, reflecting a comprehensive response to today’s evolving cybersecurity threats. A core priority of PCI DSS 4.0 is securing customer-facing environments, particularly against browser-level threats. The standard addresses rising concerns, such as online skimming and Magecart-style attacks, urging businesses to implement proactive protections.
If you’re not sure where to start, here’s what you can do:
- Conduct a gap assessment: Compare your current setup against the new 4.0 controls to identify areas that fall short. Prioritize high-risk gaps, such as inadequate browser security, weak encryption, or missing documentation.
- Update and document security policies: Revise existing policies to reflect new controls such as continuous monitoring, stronger authentication, and secure software development practices. Make sure all updates are formally documented for auditors and internal accountability.
- Strengthen customer browser security: Implement client-side security solutions to detect online skimming or Magecart-type attacks. Use Content Security Policies (CSPs) and Subresource Integrity (SRI) to ensure scripts aren’t compromised.
- Implement automated monitoring and logging: Use tools to automatically track system logs, detect anomalies, and ensure data integrity. PCI DSS 4.0 stresses continuous risk analysis, not just periodic checks.
See: What is PCI Compliance?
Strong Customer Authentication (SCA)
SCA is a requirement under the European Union’s Revised Payment Services Directive (PSD2), designed to reduce fraud and enhance the security of online transactions. It mandates that customers use at least two of the three verification factors: something they know (such as a password), something they own (like a smartphone), or something they are (like biometrics).
SCA is especially important for European e-commerce businesses and payment service providers, as it directly impacts the customer checkout experience and is legally enforced within the EU.
General Data Protection Regulation (GDPR) and consumer data protection laws
The GDPR applies to any business that handles the personal data of EU citizens, regardless of the business’s location. For online payments, this means that collecting, processing, and storing customer data (such as names, emails, addresses, and payment details) must be done with explicit consent, transparency, and accountability.
GDPR requires that data is minimized, encrypted, and stored securely, and gives consumers the right to access, correct, or delete their data. Non-compliance can lead to severe fines and reputational damage.
Anti-Money Laundering (AML) and Know Your Customer (KYC)
AML and KYC regulations are global standards designed to prevent financial crimes, including money laundering, fraud, and terrorist financing. These regulations require businesses, particularly those processing high-value or cross-border transactions, to verify the identities of their customers and monitor financial activity for unusual or suspicious behavior.
For online payments, AML and KYC measures ensure that transactions are not only legitimate but also traceable, adding a critical layer of security and compliance to e-commerce platforms, digital wallets, and financial service providers.
ISO/IEC 27001
ISO/IEC 27001 is an internationally recognized standard for Information Security Management Systems (ISMS). It provides a structured framework for identifying, managing, and mitigating information security risks across an organization.
For online payment environments, achieving ISO 27001 certification demonstrates a company’s commitment to protecting sensitive data, including payment credentials and customer information. It also strengthens a business’s security posture and builds trust with stakeholders by showing that robust security controls and governance are in place.
Online payment security best practices
Overall, businesses that implement the latest online payment security measures are already in line with best practices. However, if you’re short on time or budget, below are the fiveeasiest and most essential steps you should prioritize:
- Implement SSL/TLS encryption site-wide: This encrypts data in transit, protecting it from interception and tampering.
What to do: Use a valid SSL/TLS certificate to ensure all pages (especially checkout and login) are accessed via https://.
- Use tokenization for payment data: This minimizes the risk of data breaches and simplifies PCI DSS compliance.
What to do: Work with a payment gateway that supports tokenization to avoid storing raw cardholder data.
- Enable multi-factor authentication (MFA): This adds an extra layer of protection against credential theft and unauthorized access.
What to do: Require MFA for admin logins, customer accounts, and access to payment systems.
- Monitor transactions with fraud detection tools: This helps prevent chargebacks, detect bot attacks, and stop fraud before it completes.
What to do: Deploy real-time fraud detection systems that flag unusual behavior (e.g., location mismatches, rapid-fire orders).
- Stay compliant with PCI DSS and data privacy laws: This ensures legal compliance, builds customer trust, and avoids costly fines or reputational damage.
What to do: Regularly review and update your security policies to align with PCI DSS, GDPR, CCPA, and other applicable regulations.
Emerging Trends in Payment Security
Rise of biometric authentication
Biometric authentication is being increasingly adopted in online payment systems as a means to enhance both security and the user experience. It verifies a person’s identity using unique biological characteristics, such as fingerprints, facial features, voice, or iris patterns, instead of relying solely on passwords or PINs. The biometric authentication market is expected to reach $108 billion by 2031.
Takeaway: Leverage platforms like Apple Pay, Google Pay, or your own app’s biometric API support to reduce cart abandonment, meet PSD2/SCA compliance (if operating in the EU), and enhance protection against credential theft.
AI & machine learning in real-time fraud detection
Artificial Intelligence (AI) and Machine Learning (ML) are transforming online payment security by enabling real-time detection and prevention of fraudulent transactions. Unlike traditional rule-based systems that rely on predefined conditions (e.g., flagging any transaction over $1,000), AI/ML models learn from historical data and evolve continuously, detecting subtle, complex patterns that indicate fraud.
Takeaway: Deploy an AI-powered fraud detection solution that integrates with your payment gateway or e-commerce platform (e.g., Stripe Radar, Sift, Forter, or Riskified). Customize risk thresholds based on your business model and regularly review flagged transactions to fine-tune detection accuracy.
See: 6 Best Payment Processing Companies
Blockchain for fraud-proof transactions
Blockchain technology provides a robust foundation for enhancing secure, transparent, and tamper-resistant online payment systems. Originally designed to support cryptocurrencies like Bitcoin, blockchain’s decentralized structure and cryptographic integrity make it increasingly attractive for securing e-commerce and digital payment workflows. As of 2025, 85 million people worldwide use a Blockchain wallet.
Takeaway: Start small; use blockchain for high-value transactions, digital products, or crypto-accepting customers, and ensure you communicate the benefits (e.g., transparency, reduced fraud) clearly at checkout.
Also see: Top Payment Trends Shaping the Future of Transactions
FAQs
How do I make sure my online payment is secure?
Use trusted payment methods (such as credit cards or digital wallets), ensure the website uses HTTPS, and avoid entering payment details over public Wi-Fi networks. Always enable multi-factor authentication (MFA) and regularly monitor your transactions.
How can I tell if a website is secure for online payments?
Look for a padlock icon in the browser’s address bar and ensure the URL begins with “https://”. Secure websites also typically utilize reputable payment gateways and offer transparent privacy and refund policies.
How does encryption protect online payments?
Encryption scrambles sensitive data, such as credit card numbers, into unreadable code during transmission, so even if intercepted, it cannot be used by attackers. This ensures that your personal and financial details remain private and secure.
What should I do if I suspect fraudulent activity on my account?
Immediately contact your bank or payment provider to report the suspicious activity and, if necessary, freeze your account. Change your passwords, enable fraud alerts, and review your recent transactions for further unauthorized activity.

