Threat actors are spoofing AI chatbots and solution providers to distribute ransomware, Cisco Talos revealed on Thursday. The threat intelligence research team detailed three notable threats: CyberLock, Lucky_Gh0$t, and a new malware they named Numero.
All three find victims through fake installers for AI services, which the threat actors push to the top of search results by gaming SEO.
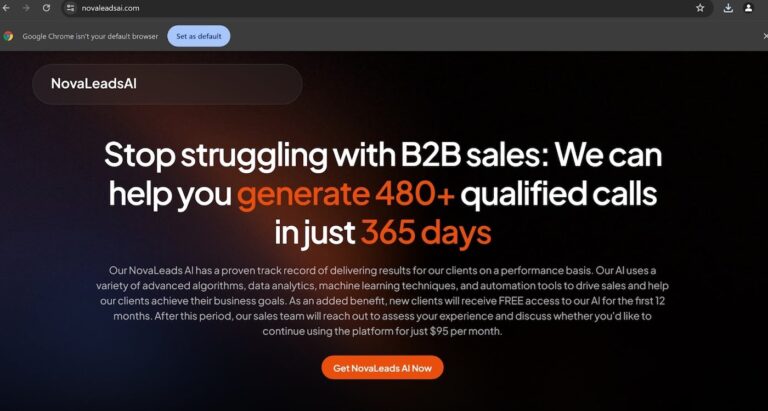
Cyberlock hides behind a fake site that looks like NovaLeadsAI
One malicious URL spoofed NovaLeadsAI, a service for business-to-business sales. The threat actors used a .com top-level domain instead of the .app top-level domain used by the real site. Because the threat actors manipulated SEO practices, the fake website was likely to appear in the top search results for related terms in search engines.
The threat actors use a ransomware strain called CyberLock, which encrypts specific files on the user’s device,” Cisco Talos said in a statement. “If their device is infected, the user will see a message demanding a ransom in exchange for the return of their “sensitive business documents, personal files and confidential databases.”
The threat actor set the ransom at $50,000, paid in Monero cryptocurrency. To add a psychological element, they falsely claimed the money would be used for humanitarian aid in places such as Palestine, Ukraine, Africa and Asia. The threat actor’s pattern of attack included threatening to expose the locked documents, although Cisco Talos found no proof the ransomware code included the functionality to do so.
SEE: Threat actors planted hidden prompts in the GitLab Duo AI assistant to steer it toward phishing links and fake URLs.
LuckyGhost hides inside a ‘ChatGPT installer’
The LuckyGhost ransomware disguises itself as a download for a so-called full version of ChatGPT, specifically a file named ‘ChatGPT 4.0 full version – Premium.exe.’ The real ChatGPT chatbot can be accessed online for free. The LuckyGhost package includes the ransomware executable and some open-source Microsoft tools for working with AI in Azure.
If installed, LuckyGhost locks up files of various types, including Microsoft Office and Adobe content, media and images, and backup and database files.
Numero spoofs online platform InVideo AI
Another malware, known as Numero, masquerades as the online platform InVideo AI. Numero prompts the user to download a malicious file, using the InVideo AI name in the file’s metadata. If installed, the fake installer deposits an executable called ‘wintitle.exe’, a malicious Windows batch file, and a VB script onto the device. Cisco Talos provided indicators of compromise in a GitHub repository.
These malware strains serve as a reminder to be cautious of links — especially product listings at the top of search engine results — and to thoroughly examine URLs, websites, and apps before downloading any files.
“Organizations and users must exercise extreme caution, meticulously verify sources, and rely exclusively on reputable vendors to avoid falling prey to these threats,” cybersecurity researcher Chetan Raghuprasad wrote in a blog post.